What are Allowlist, Denylist, and Deny Exception List in WafCharm?
Managing IP access control is a crucial part of web application security. WafCharm, AWS WAF managed service, offers three key IP address control functions — allowlist, denylist, and deny Exception List — that help organizations simplify WAF configuration and minimize false positives.
WafCharm offers three IP address control functions.
- Allowlist: Allows requests from listed IP addresses. Think of it like an office keycard: if you have a keycard, you can enter the office. Similarly, IP addresses added to the allowlist are automatically approved.
- Denylist: Blocks requests from listed IP addresses. Imagine a security guard stopping strangers at the entrance; any IP address on the denylist will be blocked.
- Deny exception list: Allows certain IP addresses to bypass the denylist. Think of it as an individually issued entrance pass: even if the denylist would normally block you, you can enter as long as you pass standard checks. In WafCharm terms, these “checks” refer to inspections performed by WafCharm rules other than denylist rules.
Since the allowlist and deny exception list have overlapping roles, users often wonder which one to use. We will break down the use cases for allowlist and deny exception list to take a closer look at how each works in different use cases.
Use Cases for Allowlist
As explained in the section above, you add IP addresses that you want to allow access to the allowlist. There is no inspection by WafCharm rules since the main goal is to automatically allow specific IP addresses. Here are some examples.
Use Case 1: Protecting Administrator Tools, such as CMS, with WAF
When using tools like a Content Management System (CMS), administrators handle various types of content and input data. Depending on the values entered, false positives from the WAF can occur.
Since access to tools like CMS is usually limited to specific users, you can add their IP addresses to the allowlist. This ensures legitimate administrative actions are not blocked while still maintaining security.
Use Case 2: Conducting Security Assessments (Sending Suspicious Requests Without WAF Intervention)
When performing security assessments or tests, you may need to send suspicious requests without interference from the WAF. While one option is to use a path not protected by WAF, this is not always possible. In such cases, you can add the IP address used for the assessment to the allowlist, ensuring your requests are allowed through the WAF.
With WafCharm, allowlisting can bypass inspections performed by WafCharm rules, allowing assessments to proceed without being blocked.
Use Case 3: Emergency Response to False Positives
When a false positive occurs due to denylist entries or WafCharm rules, you can add the affected IP address to the allowlist. This allows legitimate requests to pass through while you investigate and remediate the issue.
Use Cases for Deny Exception List
The denylist exception list allows you to add IP addresses that you don’t want to be blocked by the denylist. The main purpose is to prevent denylist rules from blocking these IPs, so they bypass denylist inspections entirely.
For example, if an IP address (e.g., x.x.x.2) is added to both the denylist and the denylist exemption list, the denylist will not block it.
Note: If the IP triggers other WafCharm rules, those rules may still apply.
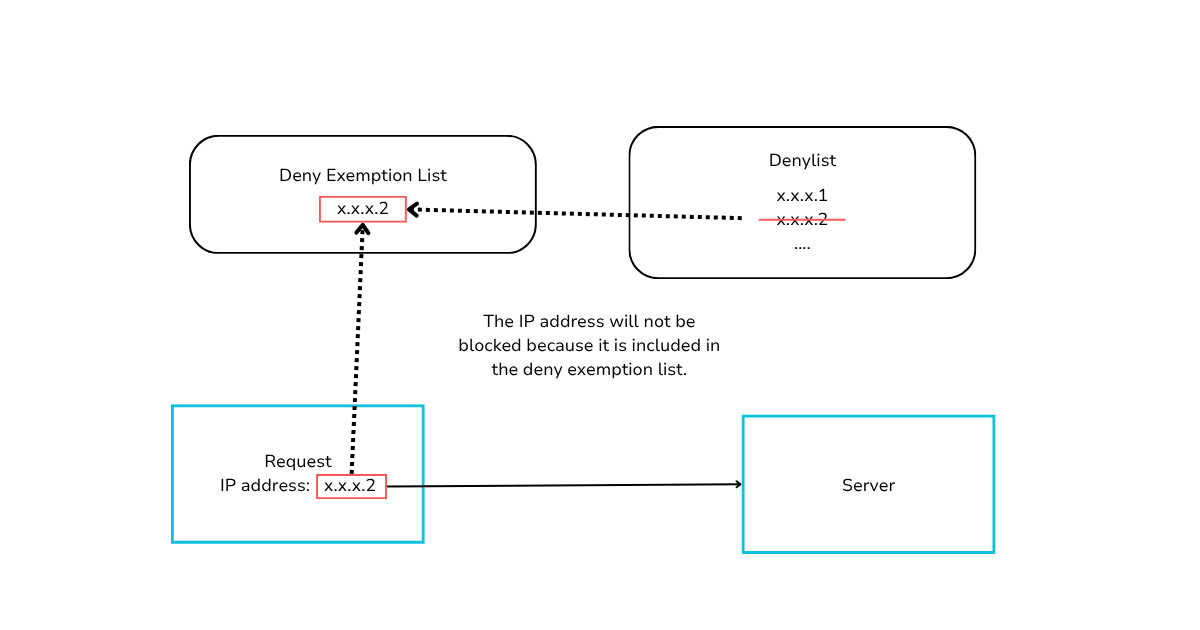
The specific behavior of the denylist and denylist exception list may vary depending on the platform and the rules you use, but the core principle remains the same: IP addresses on the denylist exception list will not be blocked by the denylist.
IP addresses not included in the denylist exemption list will have their requests blocked if they match denylist rules.
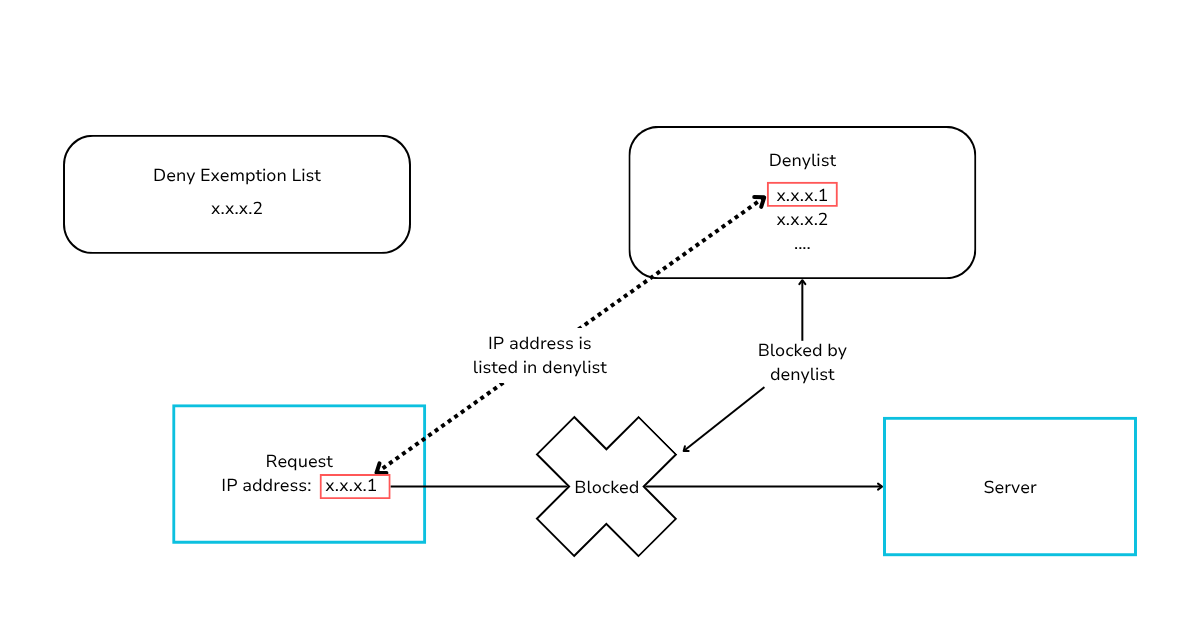
Here are some use cases for deny exception lists.
Use Case 1: Conducting Security Assessments and Tests (With WAF in the Path)
When running security assessments and tests, suspicious requests are often detected by the denylist. Once an IP address is added to the denylist, subsequent requests from that IP are blocked, which can slow down testing and assessment tasks.
If you need to conduct assessments with the WAF active in the path, it is recommended to use the denylist exemption list. This ensures that your test IPs are not blocked by the denylist while still allowing WAF protection to remain in place. By adding the IP addresses of the request origin to the denylist exemption list before running tests, you can prevent the denylist from interfering with your assessments.
Use Case 2: Using in Development or Testing Environments
The denylist exception list can be effectively used when sending specific requests for development or testing purposes that might be falsely flagged by the denylist. By adding the IP addresses of stakeholders involved in development or testing, you can prevent unexpected blocks and ensure smooth workflows.
Use Case 3: Working with External Services and Partners
When working with external services or partners, you may want to prevent false detection of health checks and auditing requests. By adding their IP addresses to the denylist exception list, you can avoid false flagging and ensure legitimate traffic is not blocked.
Use Case 4: Emergency Response to False Detection
When a false detection occurs on the denylist, you can mitigate it by using the deny exception list. This is useful when the affected IP addresses cannot be added to the allowlist, or when you want to continue investigating WafCharm rules while implementing prevention plans.
Bottom Line
Both the allowlist and deny exception list serve important roles in managing IP access within AWS WAF via WafCharm.
While their functions overlap, the key difference lies in intent:
- Use allowlist when you always want to approve a specific IP address.
- Use deny exception list when you want to temporarily bypass denylist restrictions without removing an IP from the denylist.
You don’t need to add the same IP address to both lists — once added to either, the IP will not be blocked by the denylist.
Have more questions?
If you’d like to learn more about optimizing your AWS WAF configuration with WafCharm, reach out to our team.
Contact Us

.png)
.png)

