This blog breaks down the key differences between AWS WAF and WafCharm. Discover how WafCharm manages AWS WAF operations—reducing up to 30 hours of manual workload per month—while enhancing your web application security.
What is WAF?
A Web Application Firewall (WAF) is a security service that detects and blocks attacks targeting web application vulnerabilities. By implementing a WAF, organizations can reduce risks such as data breaches and data tampering by preventing common threats like SQL injection and cross-site scripting (XSS).
What is AWS WAF?
AWS WAF is a Web Application Firewall provided by Amazon Web Services (AWS) that protects web applications running in the AWS environment. It offers high compatibility with AWS services and advanced security features, making it the recommended choice for users operating within AWS.
AWS WAF offers a variety of functions to help protect web applications. By combining different statements (rules that define detection conditions) and actions, you can prevent advanced attacks. Additionally, you can block access from specific IP addresses or countries to strengthen your security posture.
Many businesses are implementing AWS WAF to protect their applications for its easy implementation and advanced functions to protect different types of attacks.
AWS WAF Operational Challenges
Because AWS WAF offers a wide range of functions, organizations need specialized knowledge to use it effectively. It is essential to understand the basic rule structures of statements and actions, labeling features, and AWS WAF–specific functionalities to fully leverage its capabilities.
Operation, including rule updates and blocklisting, is also critical to improving the accuracy and effectiveness of AWS WAF.
Blocklisting involves identifying unauthorized access attempts and suspicious IP addresses, then adding them to a blocklist. To maintain strong protection, it is important to update and manage the blocklist regularly to ensure unauthorized access is consistently blocked.
However, these AWS WAF operations are complex and require expert knowledge of both AWS WAF and cloud security, often necessitating dedicated personnel to manage them. As a result, many organizations struggle to fully leverage the capabilities of AWS WAF effectively and this is where WafCharm comes in.
What is WafCharm?
WafCharm is a managed service that combines AI-driven automation and human experts to efficiently manage and operate AWS WAF. It also supports Azure WAF and Google Cloud Armor.
WafCharm is not a WAF itself, but it manages AWS WAF operations, significantly reducing the workload required to manage and maintain WAF settings.
3 Key Features of WafCharm
By implementing WafCharm, organizations can reduce AWS WAF operational workloads by up to 30 hours per month. In this section, we will introduce the three key features of WafCharm.
1. Manage AWS WAF Efficiently with Minimal Resources
By implementing WafCharm, you can automatically apply rules to protect against common web attacks such as the OWASP Top 10. With WafCharm handling rule management and automatic updates, your security team can stay focused on higher-value tasks while maintaining strong and consistent web protection.
Additionally, the signature matching feature can automatically add the source of unauthorized access attempts and suspicious IP addresses to the blocklist. With WafCharm, there is no need to manually manage or update the blocklist.
WafCharm also offers additional features such as tamper detection and Bot Control. It allows you to easily configure rules to block specific IP addresses or traffic from specific bots, reducing the workload for your security engineers.
2. Easily Grasp Security Status with WafCharm Console
The WafCharm console dashboard provides a clear view of WAF detections, allowing you to quickly understand the types of attacks and threats targeting your applications.
WafCharm also includes log search functions for deeper analysis. By filtering logs by time, rules, or accessed paths, you can intuitively investigate and analyze WAF activities.
With WafCharm, there is no need to manually analyze WAF detection logs using AWS services like Amazon Athena or CloudWatch Logs, reducing the resources required to identify threats and visualize detections.
3. Peace of Mind with Customer Support
WafCharm provides 24/7, year-round customer support, giving you peace of mind when dealing with incidents such as false positives or other issues. Our customer support team handles investigations and rule adjustments on your behalf, ensuring your WAF operates smoothly and efficiently.
WafCharm also handles custom rule configurations and adjustments for specific vulnerabilities and threats, so your team doesn’t need to create custom rules from scratch.
Reduce 30 Hours of Monthly WAF Operation Effort
With WafCharm, you can reduce up to 30 hours of manual WAF management per month.
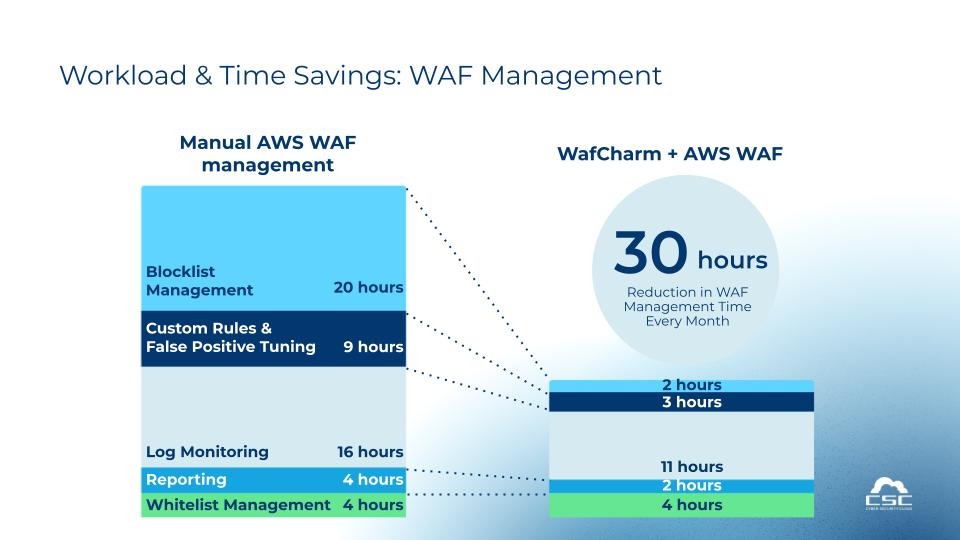
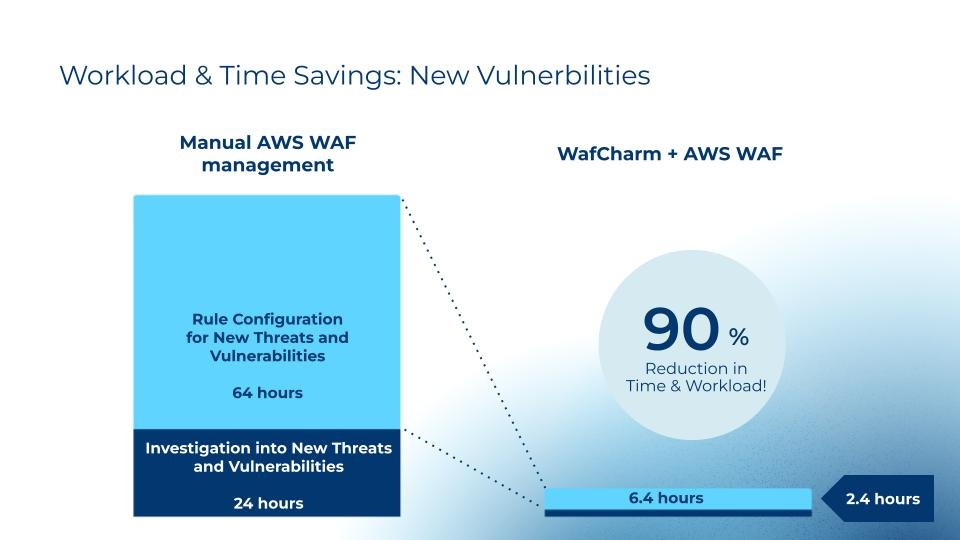
Additionally, WafCharm can cut up to 90% of the manual workload associated with custom rule creations for new vulnerabilities.
Visit our pricing page to quickly see how much cost and time you can save with our solutions.
Start Your Security Journey Here
We currently offer a 30-day free trial and 11 months 50% off of the full WafCharm solution for selected startups and SMBs.
Request a Demo to Get Started

.png)


.png)