Introduction
As digital systems grow more complex and diverse, cyberattacks are becoming increasingly sophisticated and expanding in scope. To protect cloud environments against these evolving threats, it is essential to implement comprehensive security measures that involve multiple layers of defense, rather than relying on a single approach.
In this blog, we will break down the challenges your organization may face when deploying security measures on AWS, and explain how to address them by leveraging AWS security services and AWS partner solutions.
Understanding the Security on AWS
Before we consider specific strategies, there is one important concept you should understand about security on AWS: Shared Responsibility Model.
Under this model, responsibilities are divided between AWS and the customer depending on the service being used. For example, with managed services such as AWS Lambda, AWS is responsible for the infrastructure layer, operating system, and platform—so customers do not need to worry about tasks like OS patching. However, when using services like Amazon EC2, customers are responsible for patching the operating system themselves.
When planning security measures on AWS, customers must first identify specific areas that require protection and then implement appropriate safeguards for each. However, deploying these measures is not always straightforward—there are several challenges that organizations often encounter along the way.
So what are these challenges? Let us take a closer look.
Challenges with Strategizing Comprehensive Security
The first challenge is identifying the right solution that aligns with your security strategy.
Let’s say you identified the areas that require protection and its security strategy. However, many organizations often face additional costs and effort in searching, evaluating, and selecting the most suitable tools to execute it. For example, some solutions provide threat detection but lack the ability to prevent or mitigate attacks. Others may be effective at protecting applications, yet do not offer protection at the network level.
The second challenge is the shortage of skilled security personnel. Security is a continuous effort, and implementing measures across a wide range of areas requires dedicated expertise. However, the number of engineers with specialized security knowledge is limited, often leading to security gaps and ineffective operations, ultimately increasing the risk of a potential security incident.
In the next section, we will explain how AWS services and AWS partner solutions can help overcome these challenges.
Security Strategies Leveraging AWS Services
AWS offers a wide range of services to help organizations effectively address different security challenges. These security, identity, and compliance services can be grouped into five key categories:
1. Identity and Access Management
2. Detection and Mitigation
3. Network and Application Protection
4. Data Protection
5. Compliance
This blog will not cover all of these services, but by selecting and combining the services that best suit your needs, you can address security risks efficiently. For example, Amazon GuardDuty can detect security threats, and AWS Network Firewall can provide granular control over network traffic in Amazon Virtual Private Cloud (Amazon VPC).
Additionally, Amazon GuardDuty, Amazon Inspector, AWS Config and other AWS security services can aggregate alerts and enable centralized management on Amazon Security Hub, making it easy to manage all together.
Examples of AWS Security Service to Improve the Efficiency of Security Measures
In this section, we will highlight Amazon Security Lake as one example of an AWS service that helps organizations effectively deploy security measures.
Amazon Security Lake is a fully managed security data lake service. It enables you to centralize and manage a wide variety of security data, including AWS service logs, cloud environments, on-premises systems, and third-party solutions in one place.
Amazon Security Lake also uses Open Cybersecurity Schema Framework (OCSF), an open standard. It normalizes logs to comply with OCSF, making it easier to integrate collected data with other AWS services and third-party security solutions. Specific use cases with AWS services include:
- Simple analysis with Amazon Athena
- Security log analysis and visualization with SIEM solutions on Amazon OpenSearch Service
In addition, Amazon Security Lake enables more effective security operations when integrated with third-party security vendor solutions.
Cyber Security Cloud’s CloudFastener is a prime example solution that enhances efficiency and streamlines security operations.
Comprehensive and Effective Security with CloudFastener
CloudFastener is a fully managed security service that helps organizations operate and protect their AWS environments by leveraging a wide range of AWS security services—such as Amazon Security Lake, Amazon GuardDuty, and AWS CloudTrail—tailored to each customer’s specific environment.
CloudFastener identifies assets within the AWS environment and continuously monitors for security risks. This includes analyzing operating system and software vulnerabilities, detecting misconfigurations, and performing detailed threat log analysis. In addition, it provides 24/7 monitoring and protection for AWS environments, prioritizes risks based on severity, and delivers appropriate support and guidance in response to security alerts.
Smooth implementation process leveraging AWS Service
CloudFastener can be implemented by leveraging and connecting various AWS services within the customer’s AWS environment without the added effort of integrating external services. This approach delivers high cost performance, while ensuring seamless operation. Importantly, CloudFastener itself is built natively on AWS.
The following is a customer reference example of an AWS architecture when integrating with CloudFastener.
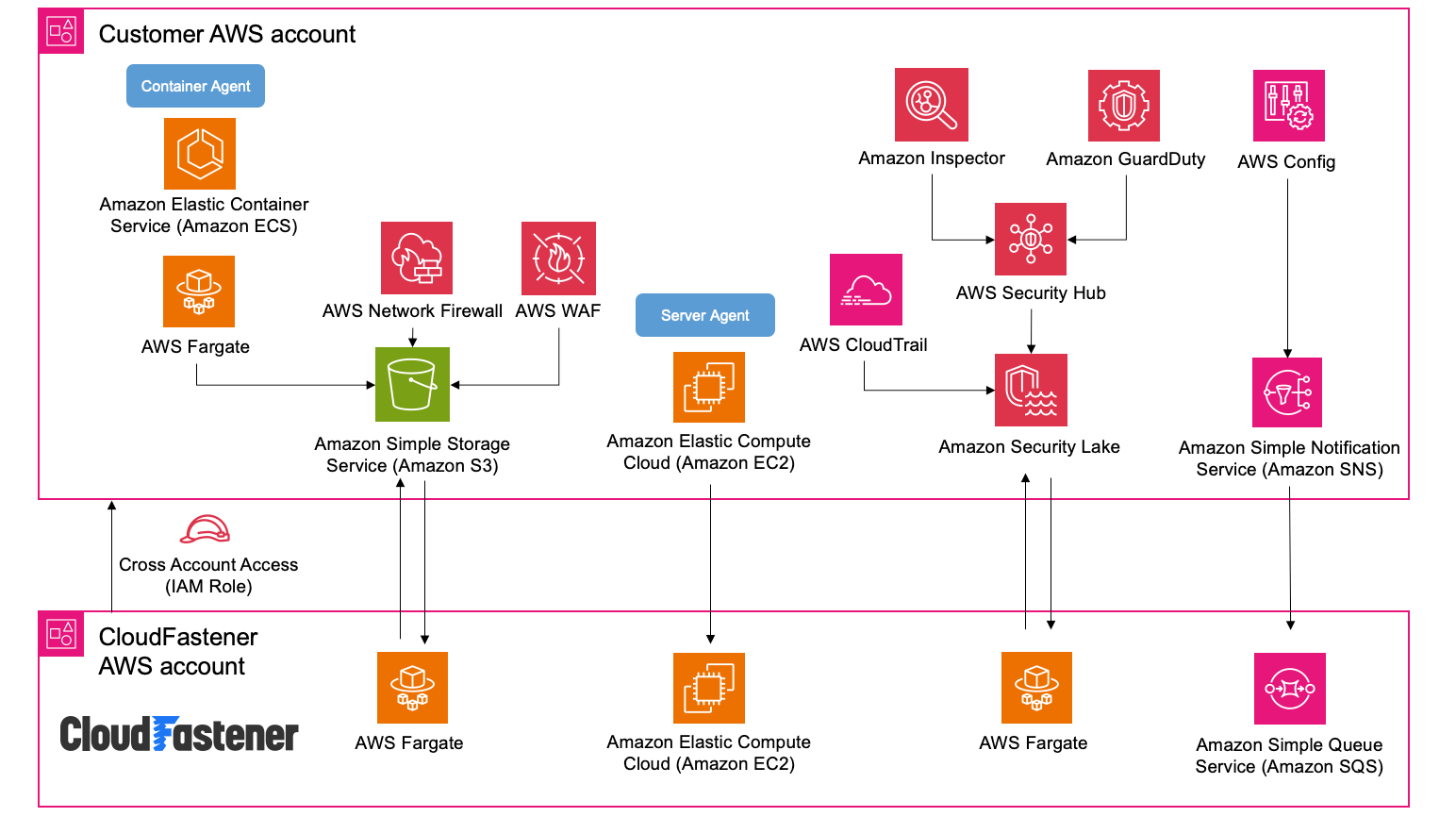
Graphic 1: Example Architecture streamlining customer AWS account and CloudFastener
For example, CloudFastener functions as an Amazon Security Lake subscriber, collecting and analyzing data from services such as AWS Security Hub, Amazon Inspector, Amazon GuardDuty, and AWS CloudTrail through Amazon Security Lake. As a result, the only action required from the customer is to unify the logs from each service and connect them to CloudFastener.
The connection is established securely using a cross-account IAM role, and we also provide a CloudFormation template to simplify the creation of this role. Similarly, other functions are designed to significantly reduce the effort required for integration by leveraging and combining AWS services and features.
With CloudFastener, security engineers conduct an initial assessment to evaluate the current state of security measures and identify both known and hidden security challenges. Based on this assessment, customers can flexibly select and combine only the AWS services they need, while also receiving support for activating security services and resolving security alerts.
In addition, it helps organizations apply security best practices quickly by using the AWS Security Maturity Model, a framework that measures the extent to which security measures are being implemented.
In this way, CloudFastener not only streamlines integration with AWS services, but also provides the support needed to deploy security measures effectively. This reduces the effort required to initiate security operations and ensures that your measures are aligned with best practices.
All-in-One and Continuous Security Measurement with Security Engineers and AI
CloudFastener includes built-in AI, enabling an all-in-one security approach that combines both identification and protection, capabilities that are often not covered by traditional security managed services.
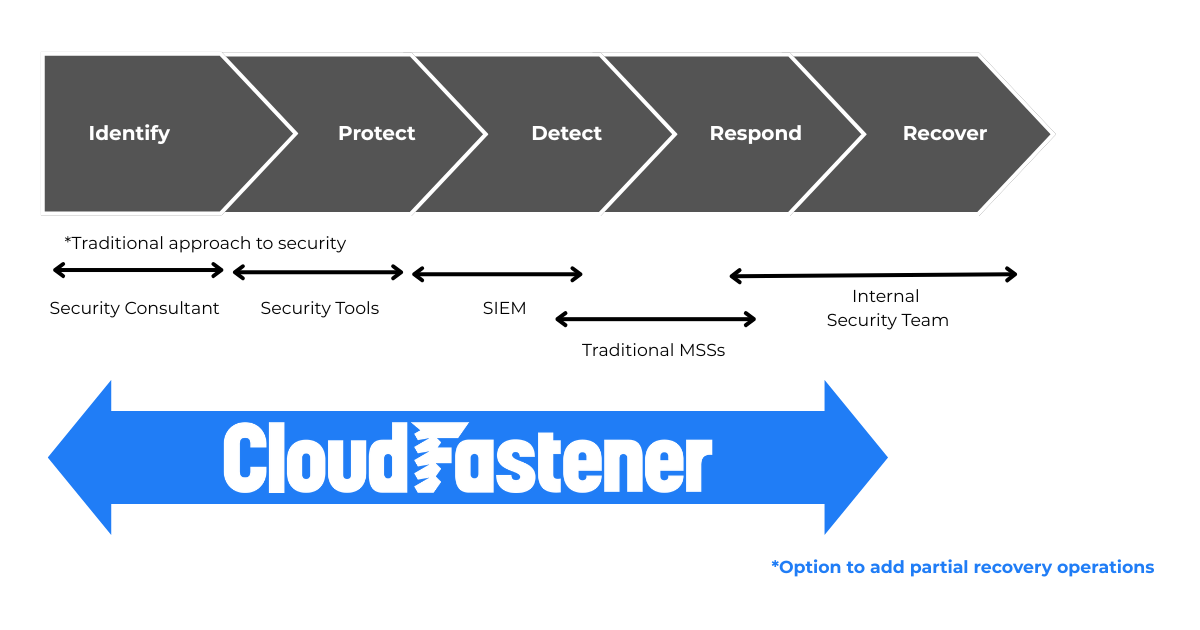
Graphic 2: CloudFastener Coverage Areas
For example, by deploying dedicated agents on Amazon EC2 instances and for container services, CloudFastener can detect and alert on file tampering and unauthorized access occurring on EC2. In containers, it not only detects and notifies any anomalous behavior that violates predefined rules by monitoring system calls, but also protects the container runtime by automatically blocking malicious system calls. Furthermore, these events are monitored 24/7 throughout the year, with customers only notified of threats that truly require action, while CloudFastener handles and resolves them.
Monitored resources can be centralized using the Resource Inventory, a standard feature of CloudFastener, and unmanaged resources can also be identified, providing an effective measure against Shadow IT.
With the vulnerability scanning feature, Cyber Security Cloud can use both AWS WAF and AWS Network Firewall to create custom signatures based on the scan results, which is typically very time-consuming to perform manually.
In this way, CloudFastener enables comprehensive and efficient security management by taking over AWS security data collection and operations that usually require significant labor and specialized expertise.
Bottom Line
Comprehensive security management is essential to protect your AWS environment from evolving threats. However, organizations often face challenges such as identifying critical tasks across a wide range of responsibilities and shortages of skilled security personnel required for prevention and ongoing operations. By combining AWS security services with CloudFastener, you can achieve more efficient and effective protection of your entire AWS environment.
Start Your Security Journey Here
Get started with a CloudFastener live demo.
CTA: Request a Demo


.png)

.png)